3. Configuring the Firewall
There are three ways to deploy your TM-200, TM-500, TS-300, TM-800, TM-1000, TS-700, or TS-900 RHUB appliance:
- Outside the Firewall
- Inside the Firewall and Accessible by Users outside Firewall
- Inside the Firewall and not Accessible by Users outside Firewall
Depending on the deployment, you may or may not need to configure your firewall.
3.1 Behind Firewall and Accessible by Users outside Firewall
This deployment (Figure 3.1) is most popular and it is typically done by connecting RHUB appliance with the DMZ port of your router. You can also place the RHUB appliance anywhere on your LAN.
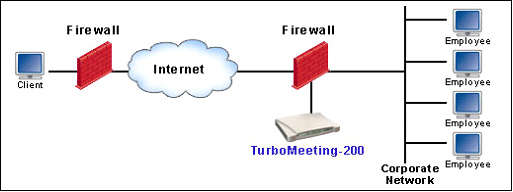
Figure 3.1 Inside Firewall and Accessible by Users outside Firewall
In order for external users to access your appliance, you need to open the inbound TCP ports: 80, 443 and 8889 on your firewall/router and forward the inbound TCP traffic on these ports to the corresponding ports of the local IP address of your RHUB appliance.
If you are using a SOHO or home router, opening inbound ports and doing port forwarding are fairly easy. For example, in a LinkSys router, you usually look for the “Applications” link. In a Belkin router, you look for the “Virtual Servers” link. After clicking the link, you will see a page similar to Figure 3.2. Fill in the three TCP ports (80, 443 and 8889) and your RHUB appliance local IP address. The firewall configuration is done.
In Figure 3.2, the “Private IP address” is the RHUB appliance’s local IP address, which you define when you configure the meeting server IP settings; the “Inbound port” may be called “Source port”; the “Private port” may be called “Destination port”. You can input anything in the “Description” field. Don’t forget to check the “Enable” fields.
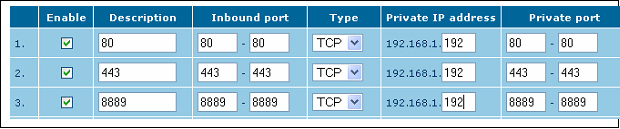
Figure 3.2 A sample of firewall configuration
This deployment gives you the maximum flexibility in terms of meeting access security control. With this deployment, you can host two types of meetings:
- Internal meetings that only users behind your firewall can join (including users in the Virtual Private Network, or VPN)
Note: You can manually allow external users by specifying a list of IP addresses
- External meetings that anyone including attendees outside your firewall can join.
|