Access security is the weakest point in hosted web
conferencing services:
Security is as good as your weakest
point: Hosted conferencing services offer little in access
security and open up meetings to nearly anyone who has a meeting
ID and a password. This “security” can easily be compromised by
reading one’s emails or having access to an associate’s calendar
(since most meeting invites are done through calendar sharing).
In contrast, RHUB servers have the ability to setup a
“virtual VPN” between the host and the attendee(s), thus
limiting the scope of the attendance to an internal
location/address or specified external IP addresses. Note that
these policies are designed to work in conjunction with your
internal security servers, such as firewalls, routers or
other security devices your Enterprise might have deployed. In
the end, RHUB servers provide total best in breed security by
brilliantly restricting attendance to authorized locations and
attendees.
Data transmission security:
For web conferencing applications, transmission security is
maintained by using strong SSL encryption alongside with each
vendor's proprietary encryption. RHUB's servers use both SSL
and proprietary encryption. The transmission of user and meeting
passwords as well as meeting IDs over the Internet is SSL
encrypted.
Deploy RHUB Web Conferencing Servers to fit your security
needs:
The best way to protect against the security breaches
described above is to use an on-premise solution where your
firewall protects your meetings. The RHUB web conferencing
servers are the most affordable solutions that fit that
purpose.
The diagrams below show three typical ways to deploy the RHUB
web conferencing servers:
- Behind the firewall: restricting it to internal meetings
only (Private cloud)
- DMZ: Designed for both internal and external meetings
- Outside firewall: Restricting it to external meetings
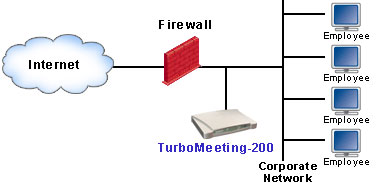
(a) Behind Firewall Deployment
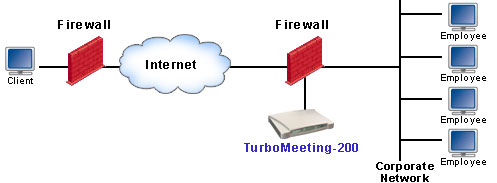
(b) DMZ Deployment
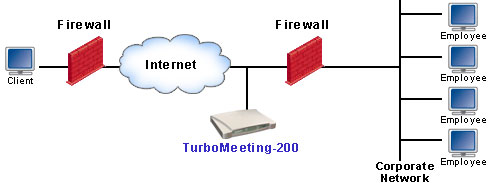
(c) Outside Firewall Deployment
Both behind-firewall and DMZ deployment offer
strong security measures. DMZ is available on almost every
router, including home routers. DMZ deployments provide great
flexibility, allowing both internal (behind firewall) and
external (outside firewall) attendees to join a meeting. When
you start a meeting, you simply check the option to restrict the
system for internal attendees only (see below diagram). In that
case, the RHUB web conferencing server will reject any
attendees accessing the system from outside your firewall.
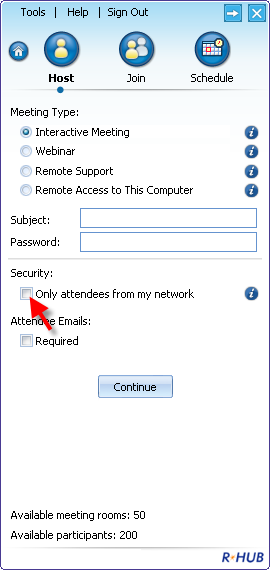
You can determine the level of security of a meeting
The outside-firewall deployment (c) is equivalent in security to
hosted services. It has the same weak access issues as hosted
services do.
|